Never Trust, Always Verify
Zero Trust Architecture
Zero Trust protects your data by continuously verifying every user, device, and connection—no matter where they are—ensuring no automatic trust inside or outside your network.
Zero Trust Architecture (ZTA) is a modern cybersecurity framework based on the principle “never trust, always verify.” It assumes that no user, device, or network is inherently trustworthy — even if it’s inside the traditional corporate perimeter.
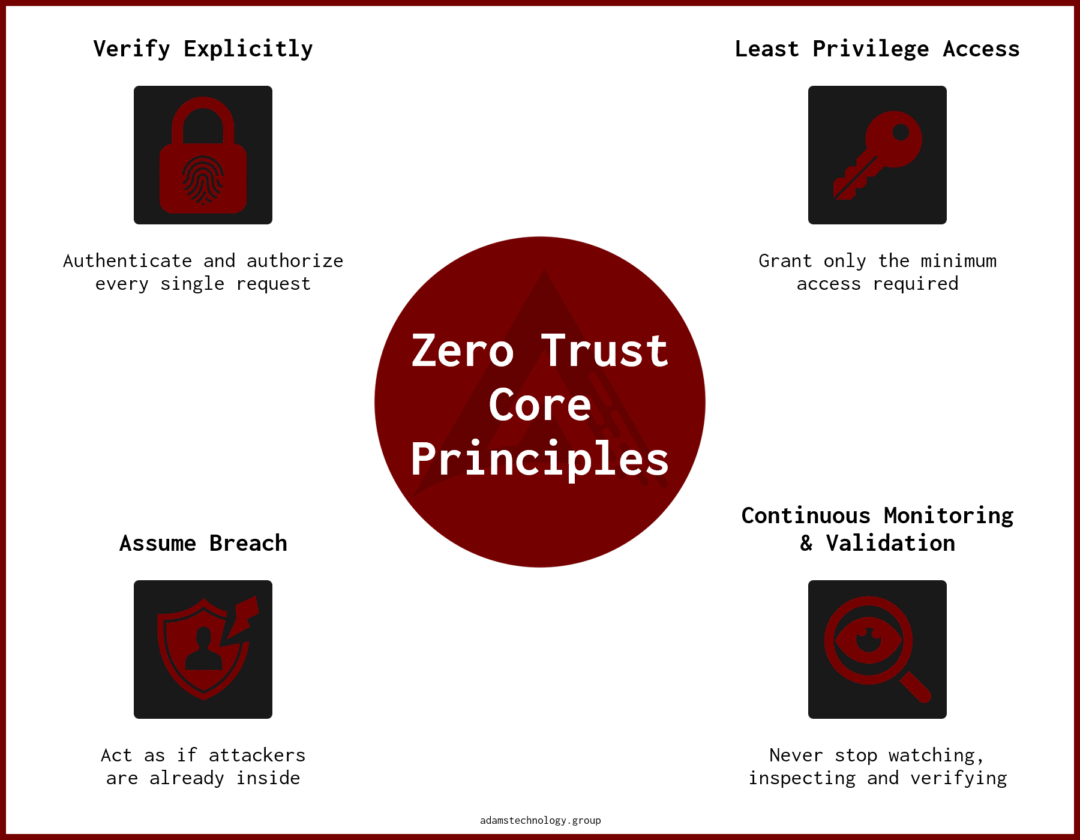
Core Principles
- Verify Explicitly
Always authenticate and authorize every request, regardless of where it comes from (inside or outside the network). - Least Privilege Access
Users and devices get only the minimum access they need, for the shortest time necessary (just-in-time and just-enough access). - Assume Breach
Design the system as if attackers are already inside the network. Limit lateral movement and segment access aggressively. - Continuous Monitoring & Validation
Constantly inspect and log traffic, user behavior, and device health. Re-authenticate and re-authorize throughout the session (not just at login).
Key Differences from Traditional Security
| Traditional “Castle-and-Moat” Model | Zero Trust Model |
|---|---|
| Trust everything inside the perimeter | Trust nothing by default |
| One-time authentication at the edge | Continuous verification everywhere |
| Broad network access once inside | Micro-segmentation and granular controls |
| Focus on keeping attackers out | Focus on limiting damage if breached |
Traditional perimeter-based security is insufficient for today’s environment of cloud services, remote work, mobile devices, and sophisticated attackers who are already inside or can easily bypass the perimeter. Zero Trust provides continuous verification of every user, device, and request regardless of location.
Main Components of Zero Trust
- Strong Identity Verification (multi-factor auth, passwordless, etc.)
- Device Compliance Checks (is the device patched, encrypted, healthy?)
- Micro-segmentation (network divided into small zones with strict policies)
- Policy Enforcement Points (gateways, proxies, or software-defined perimeters that check every request)
- Continuous Analytics & Monitoring (SIEM, UEBA, threat intelligence)
Real-World Implementations
- Google’s BeyondCorp (one of the first large-scale Zero Trust deployments)
- Microsoft’s Zero Trust strategy (integrated into Azure AD, Defender, etc.)
- Tools like Zscaler Private Access (ZPA), Cloudflare Access, Okta + micro-perimeters
Simple Way to Think About It
In the old model: “You’re in the office → you’re trusted.”
In Zero Trust: “Who are you? Is your device secure? Do you really need access to this exact resource right now?” → checked every single time.
Zero Trust is not a single product but a strategy/philosophy that combines identity, endpoint security, network segmentation, and automation to reduce risk in today’s cloud, mobile, and remote-work world.